A hands-on, production-style AWS networking project — build a secure Virtual Private Cloud (VPC) with a public Bastion Host to SSH into private EC2 instances, all within AWS Free Tier limits.
Perfect for DevOps engineers, cloud learners, and AWS certification aspirants.
- Overview
- Architecture Diagram
- Visual Reference (Screenshots)
- Key Highlights
- Components Overview
- Setup Guide (Step-by-Step)
- Screenshots Guide (Filenames)
- Learning Outcomes
- Tech Stack
- Project Structure
- Ideal For
- License
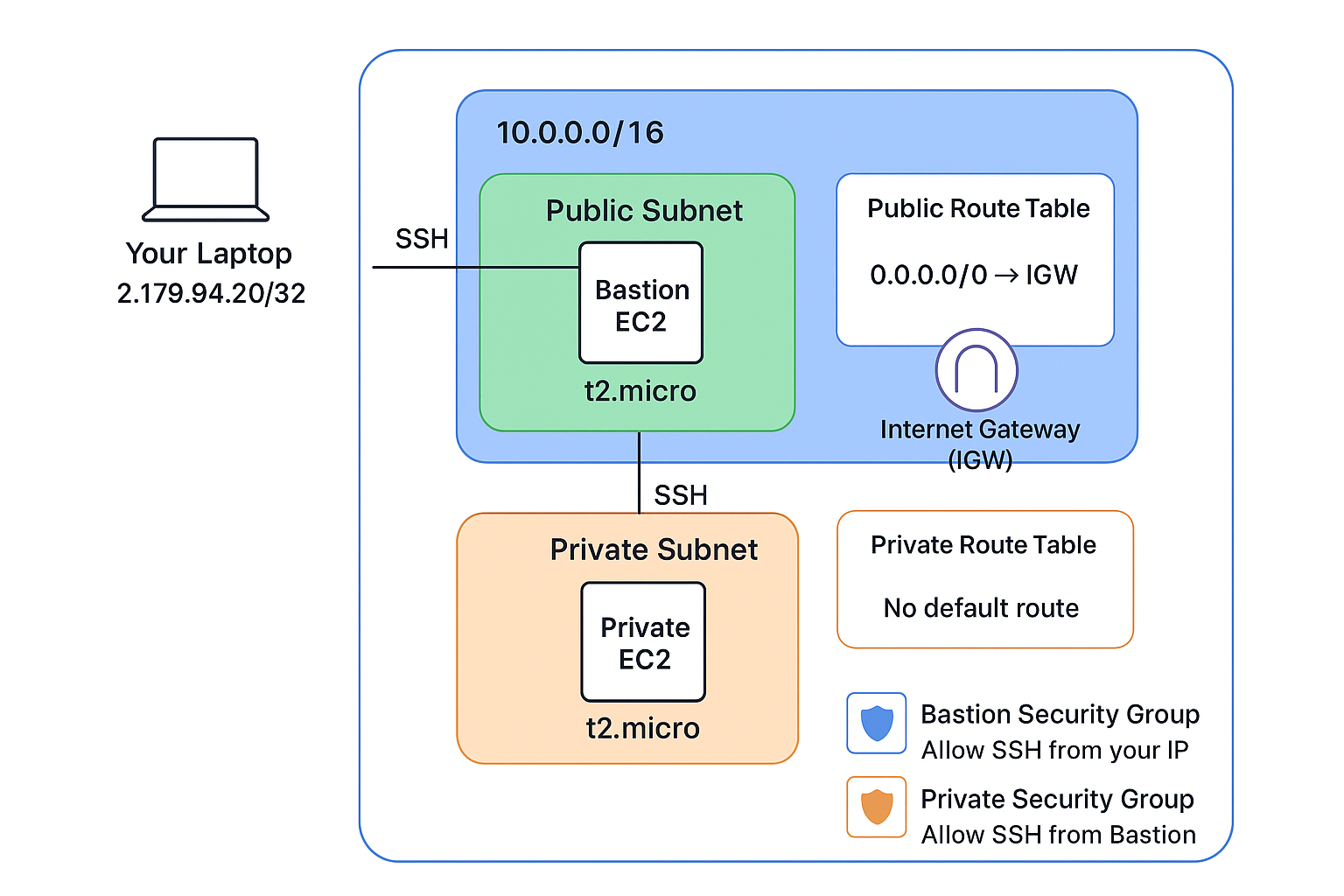
Architecture Flow:
Your Laptop → (SSH) → Bastion Host (Public Subnet) → (SSH) → Private EC2 (Private Subnet)
This project demonstrates secure access control, subnet isolation, and internal communication inside AWS — exactly how production VPCs are designed in real-world cloud setups.
Includes:
- ✅ Custom VPC (
10.0.0.0/16) - ✅ Public + Private Subnets
- ✅ Bastion Host with restricted SSH
- ✅ Private EC2 (no public IP)
- ✅ Route Tables, Security Groups, and NGINX servers
| Feature | Description |
|---|---|
| 🟢 Free Tier Safe | No NAT Gateway — uses Bastion for internal access |
| 🌍 Region | ap-south-1 (Mumbai) |
| 💻 Instances | 2× Amazon Linux 2023 (t2.micro) |
| 🔐 Security | Bastion → open only to your IP |
| ⚙️ Networking | Custom VPC with public/private subnets |
| 🧱 Web Server | NGINX running on both instances |
| 🧰 Tools Used | EC2, VPC, IGW, Route Tables, Security Groups, SSH |
| Resource | CIDR / Notes |
|---|---|
| VPC | 10.0.0.0/16 |
| Public Subnet | 10.0.1.0/24 |
| Private Subnet | 10.0.2.0/24 |
| Internet Gateway | Attached to VPC |
| Route Tables | Separate for Public & Private |
| Security Groups | Bastion ↔ Private EC2 controlled |
| SSH Key | my-key.pem |
⏱️ Time Required: 45–60 minutes
💰 Cost: Free (within AWS Free Tier)
💡 Difficulty: Beginner–Intermediate
- Name:
project-vpc - CIDR:
10.0.0.0/16
- Public Subnet:
10.0.1.0/24— Auto-assign public IP: Yes - Private Subnet:
10.0.2.0/24— Auto-assign public IP: No
- Create IGW:
project-igw - Attach to
project-vpc
💡 Purpose: Allows internet access only for public subnet resources.
- Public Route Table: Add route
0.0.0.0/0 → project-igwand associate with public subnet. - Private Route Table: Associate with private subnet — no internet route.
Bastion SG (sg-bastion)
| Type | Port | Source |
|---|---|---|
| SSH | 22 | Your public IP (x.x.x.x/32) |
| HTTP | 80 | 0.0.0.0/0 (optional) |
Private SG (sg-private)
| Type | Port | Source |
|---|---|---|
| SSH | 22 | sg-bastion (reference) |
✅ Bastion can SSH into Private EC2.
✅ Private EC2 not exposed to internet.
- Public Subnet:
public-subnet-1 - AMI: Amazon Linux 2023
- Instance Type:
t2.micro - SG:
sg-bastion - Key Pair:
my-key.pem
Connect from your laptop:
chmod 400 my-key.pem
ssh -i my-key.pem ec2-user@<BASTION_PUBLIC_IP>| Setting | Value |
|---|---|
| Name | private-ec2 |
| AMI | Amazon Linux 2023 |
| Instance Type | t2.micro |
| Subnet | private-subnet-1 |
| Public IP | None |
| SG | sg-private |
| Key Pair | my-key.pem |
Connect via Bastion (from Bastion shell):
ssh -i my-key.pem ec2-user@<PRIVATE_EC2_IP>
From your Laptop → Bastion (Public EC2):
On Bastion (Public):
chmod 400 mahesh.pem
ssh -i mahesh.pem ec2-user@<BASTION_PUBLIC_IP>
On Private EC2:
ssh -i mahesh.pem ec2-user@<PRIVATE_EC2_IP>
✅ Verify that you can SSH from your laptop to Bastion.
✅ Verify that you can SSH from Bastion into Private EC2.
✅ This confirms your VPC, Subnets, Security Groups, and Bastion Host are configured correctly.
Use AWS CLI or Console to verify resources:
aws ec2 describe-instances
aws ec2 describe-subnets
aws ec2 describe-security-groups
aws ec2 describe-route-tables
Terminate instances and delete networking resources (or delete via Console):
# Terminate instances
aws ec2 terminate-instances --instance-ids <bastion-id> <private-id>
# Delete networking components
aws ec2 delete-subnet ...
aws ec2 delete-route-table ...
aws ec2 detach-internet-gateway ...
aws ec2 delete-internet-gateway ...
aws ec2 delete-vpc --vpc-id <vpc-id>
Or simply delete everything via AWS Console.
| Step | Screenshot | Description |
|---|---|---|
| 1 | vpc-created.png |
Custom VPC creation confirmed |
| 2 | subnets.png & subnets-private.png |
Public & Private subnets with CIDRs |
| 3 | igw-attached.png |
Internet Gateway attached |
| 4 | route-table-public.png & route-table-private.png |
Public/Private route tables |
| 5 | security-groups.png & private-security-group.png |
Security Groups rules |
| 6 | ec2-bastion.png |
Bastion EC2 running |
| 7 | private-ssh.png |
Private EC2 running |
| 8 | ssh-bastion-terminal.png & private-terminal.png |
SSH: Laptop → Bastion → Private EC2 |
| Feature | Description |
|---|---|
| 🟢 Free Tier Safe | No NAT Gateway — uses Bastion for internal access |
| 🌍 Region | ap-south-1 (Mumbai) |
| 💻 Instances | 2× Amazon Linux 2023 (t2.micro) |
| 🔐 Security | Bastion → open only to your IP |
| ⚙️ Networking | Custom VPC with public/private subnets |
| 🧱 Access | Bastion → Private EC2 SSH only |
| 🧰 Tools Used | EC2, VPC, IGW, Route Tables, Security Groups, SSH |
-
Amazon VPC
-
EC2 (Amazon Linux 2023)
-
Internet Gateway
-
Route Tables
-
Security Groups
-
SSH
aws-vpc-bastion-architecture/
├── README.md
├── architecture.png
└── screenshots/
├── vpc-created.png
├── subnets.png
├── igw-attached.png
├── route-table-public.png
├── route-table-private.png
├── security-groups.png
├── ec2-bastion.png
├── ec2-private.png
├── ssh-connection.png
├── nginx-public.png
└── nginx-private.png
✅ DevOps Engineers ✅ Cloud Enthusiasts ✅ AWS Certification Prep ✅ Portfolio & Resume Boost ✅ Free-Tier AWS Labs
MIT License © 2025 Mahesh Shukla